Your cloud data needs a reality check: our investment in Cyera

The complex equation of data reality
With AWS, Azure and GCP growing 40-50% YoY at massive scale (AWS’ run rate is more than $70B!), it’s fair to say that migration to the cloud is in full swing. That said, some large sectors like financial services and healthcare only started to migrate their core workloads and data to the cloud more recently. With less than a third of workloads currently migrated, there’s still a long way to go.<sup>1<sup>
One of the benefits of the cloud is that it gives development teams more agility and flexibility, but with increased flexibility comes the downside of a loss of control and visibility. This is a particularly acute issue for data, which is the most valuable and sensitive asset of many businesses.
.avif)
On top of the move to the cloud, the volume of data continues to grow exponentially. Latest estimates are that the 65 zettabytes (1 zettabyte = 1 billion terabytes) of global data in 2020 will have nearly tripled by 2025.<sup>2<sup> With digital transformation accelerating and new AI based applications being created and perfected every day, this growth isn’t set to stop anytime soon. Add to this the constantly increasing compliance and privacy needs, including GDPR and CCPA, and the growth of cyber threats, and you end up with the following equation:
Data reality: cloud migration x growing data sets x increased compliance x cyber-attacks = big headache for CTOs and CISOs
So how do you solve this equation? You have to eliminate the headache.
Cloud security and compliance stack
We think about cloud security and compliance in four distinct layers:
1) Infrastructure layer: securing your cloud infra typically requires a CSPM solution (cloud security posture management – a tool identifying misconfiguration issues and compliance risks for your cloud infrastructure)
2) Identity layer: who can access what, typically managed by an identity management layer
3) Application layer: organisations now are increasingly applying the “shift left” principle, giving developers the tools they need to write secure code, instead of relying on security teams
4) Data layer: understanding where your sensitive data is and what policies should be applied in order to ensure that it’s safe and compliant
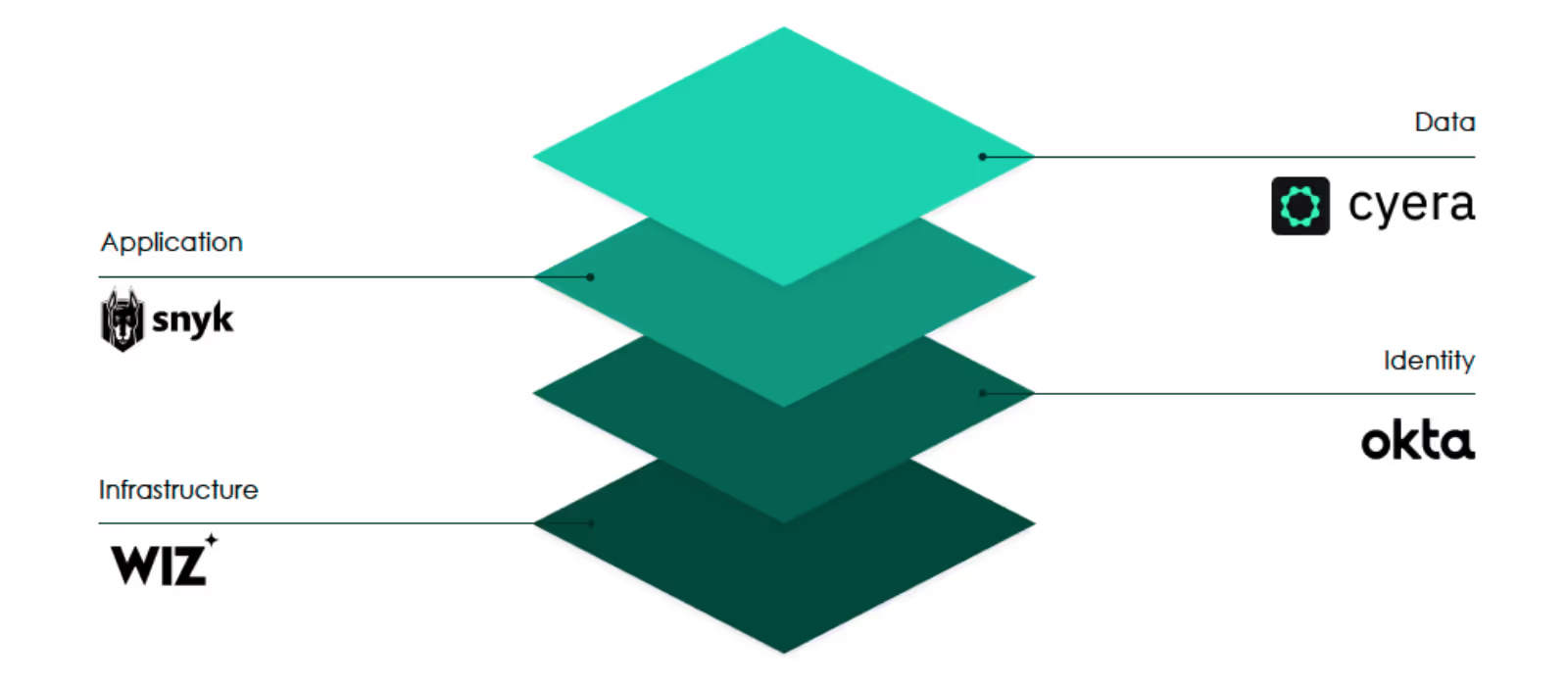
Over the past few weeks, we’ve talked to many CISOs and CTOs about cloud security and here’s what we observed:
- Regardless of whether companies are cloud-first or in the process of moving their infrastructure to the cloud, understanding and securing their infrastructure is a key priority for CISOs/CTOs. The fact that it’s so easy for employees to create cloud resources and move them around is creating “infrastructure chaos” and driving an acute visibility issue
- Most companies we spoke to already had a CSPM solution in place. Ease of set-up was a key adoption driver for these solutions
- The identity layer was well addressed and understood via solutions like Okta
- While several companies had heard of the shift left and were already deploying Snyk, others were just starting to think about it. It seems like we’re at the early inflection point of the S-curve on this front and expect the momentum to continue - and even accelerate - as large companies expand their deployments to all their development teams
- When it comes to the data layer, all companies are lacking visibility on what sensitive data they are collecting, where it's stored and whether it's at risk. The situation is untenable, leading all companies we spoke to have put cloud data security on their list of priorities for this year. Many were starting to search for a dedicated solution for the cloud data and compliance layer
Cyera: solving the data reality equation
Why is the data layer challenging to address when data security has been an established field of cyber security for such a long time?
The issue is that existing products focus on endpoints and on-premise datastores. Sub-categories include DLP (e.g. Code42, Digital Guardian), data privacy (Privacera), encryption (Enveil, Protegrity) and data security platforms (Ionic, Varonis). Many of these products rely on an agent-centric architecture which must be installed on each endpoint in order to monitor data. With the shift to cloud, a more scalable architecture is possible - and indeed required - to deal with the scale and dispersion of enterprise data. These solutions weren’t architected for the cloud at inception and don’t have the simplicity of deployment and functionality expected by cloud users. In addition to the data security pure-plays, the cloud service providers also have some data security offerings for their own clouds, including AWS Macie, but these fail to support the multi-cloud architectures favoured by most large enterprises and are also expensive to run while also not providing full coverage of the data landscape. In the case of AWS Macie for example, only S3 buckets are analysed, leaving significant risk across enterprises’ complex data environments.
The failure of existing data security solutions to address cloud specific issues are reflected by the increasing numbers of data breaches that are increasingly sophisticated and targeted. CrowdStrike recently reported an 82% increase in ransomware-related data leaks in 2021.<sup>3<sup> There is no industry or scale of enterprise which is immune from the threat of exposing sensitive data records.
We concluded it was time for a cloud native data security platform, identifying the key success factors as:
1) Platform: buyers are looking for a platform that includes discovery, accurate classification, risk assessment and remediation
2) Ease of deployment: cloud buyers expect a “plug and play” solution with very short time to value (hours/days rather than weeks)
3) Cost efficiency: the technical challenge will be to infer the key risks from data and metadata while being smart in the scope and frequency of the scans at enterprise scale to be cost efficient
When we met Cyera, we knew that we’d found the perfect team to address this new category of security. We loved the passion, drive and ambition of Yotam and Tamar, Cyera’s two founders, and could see that the data and security background from their service in the Israeli military uniquely equipped them to address this massive opportunity. With the elite initial team they’ve assembled, they’ve managed to build their first product in record time and secure large six-figure deals while still in stealth mode. Cyera’s technology is the first time we’ve seen a data solution that has such quick time to value, full coverage, and ease of deployment and it explains why the CIOs and CISOs we spoke to immediately asked us for an introduction to the company.
We’re excited to announce today that we’re co-leading a $60M round with Sequoia and Cyberstarts in the company and look forward to working closely with Yotam, Tamar and the whole Cyera team to build the leading cloud data reality platform. Thank you Yotam and Tamar for choosing to partner with us!
The Accel team,
Will, Mor and Philippe
Great companies aren't built alone.
Subscribe for tools, learnings, and updates from the Accel community.


